Computer Hacking in the New Age, All you Need to Know about Hacking
Every human discovery has pros and cons, so is the computer which has pervaded all our lives. The modern humanity is increasingly dependent on computer for various day-to-day activities. Computers do us a whole lot of good things, but it is not without some pitfalls. With the extensive use of internet for hundreds of our needs, computer opens a vicious cycle of hackers.
Computer hacking is a term which refers to an individual’s illegal and
unauthorized access to the data which are stored in a user’s system.
This is done to disturb the confidentiality and security of the user’s
computer.
The hackers focus on individuals’ computer system when they are online.
As long as you are not connected to internet you are less prone to
hacking. The access to internet has actually made computer hacking easy.
You must protect your computer with strong antivirus and firewall
programs to keep hackers away. Hackers are known for creating problems
which are difficult to solve. This gives a good business to computer
investigators and technicians. Hacking can be done in lots of ways. Few
of them are given below:
- Worms: These are the programs which propagate through networks.
- Trojans: These are hidden in websites, attached files and emails.
- Viruses: These attach themselves to various kinds of files. They can damage certain functions of your computer.
Hackers also crash on wireless networks which do not have firewall
installed and enabled. They can also send email attachments with
malicious software which get embedded on the victim’s computer. Hackers attack accounts which have weak passwords. All these are done to get access
to confidential and sensitive information of the users. Whatever is the
method of hacking, the effect is harmful for the user. Your system will
be flooded with viruses, malwares which steal your information. In
order to avoid hacking one has to make sure that the systems at home or
office have the latest anti-virus program and firewall installed and
enabled. These programs need to be regularly updated. Use the latest
browser and scan your computer on a regular basis.
New Age...
The New Age of internet has brought with it many risk factors along with umpteen advantages. The New Age
is the time where our personal lives are no longer very personal, but
people are able to access personal information of internet users from
various sources in the virtual world. We need to be careful about
usernames and passwords, else it will lead to dangerous consequences.
Universities, large companies and government agencies are mostly
targeted by hackers simply because of the bulk of information they
handle. The great newspapers like The Wall Street Journal and The New
York Times were also targeted by hackers.
Computer hackers are people who gain remote access to information stored in a system elsewhere. During the 1950s and 60s hackers were more drawn towards learning the operations of a computer rather than stealing confidential information of a remote user. Unlike the olden days, now computer hacking has become more sophisticated and organized. In the late 1990s hackers tried to get access to files in the network of Pentagon. Some more expert hackers gained access to the patent files at the Indiana University School of Medicine in February 2003. Many hackers were sentenced in the history since hacking represents a potential national security threat.
Viruses
One major tool hackers use to steal information from computer systems is
the use of viruses. Over the years the number of viruses has increased
drastically. The virtual world now has above 100000 viruses and the
number grows virtually every day. Apart from the threat the computer hackers pose, they also can be beneficial in one way. They can bring to light the flaws in a computer network. Hackers can help in redesigning the system and in making information inaccessible to illegal users and to unauthorized access.
Getting Administrative Access
Getting a log in password is one of the predominant ways to get access to a computer which is by the side of the hacker. Getting remote
access to a computer is another way to hack a system. Managing to crack
a Wi-Fi password is the third method of sneaking into someone else’s
system. Hacking if done on a public or school computer will have serious
consequences. The hacker will be put behind the bars for illegally
accessing the computer which does not belong to him or her.







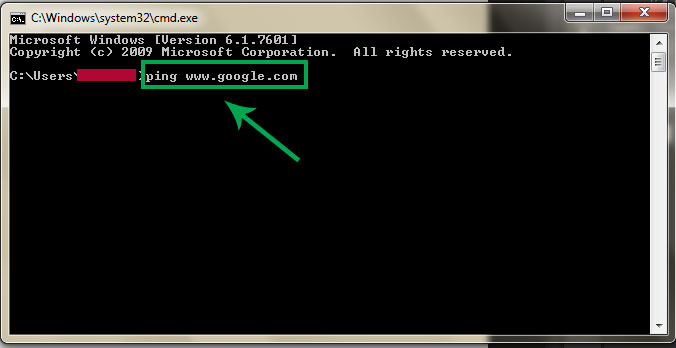
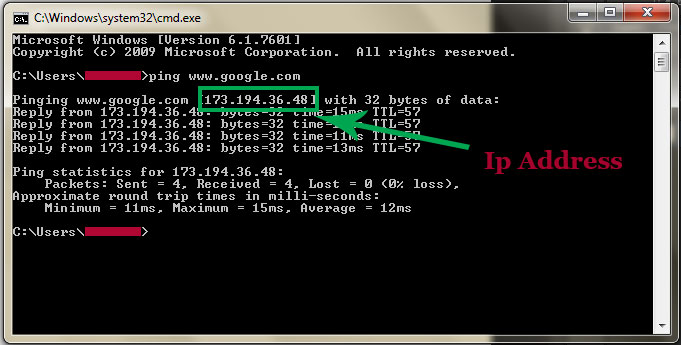








Follow Us